Network monitoring
SD-WAN network monitoring
ServicePilot provides you with a complete monitoring solution for SD-WAN networks. Get the necessary visibility into WAN connections, application flows with response times and link loads to optimize the user experience. The ServicePilot platform is a unified monitoring software that allows you to plan, monitor and predict the performance of new SDN / SD-WAN networks or hybrid and dynamic networks.
Learn more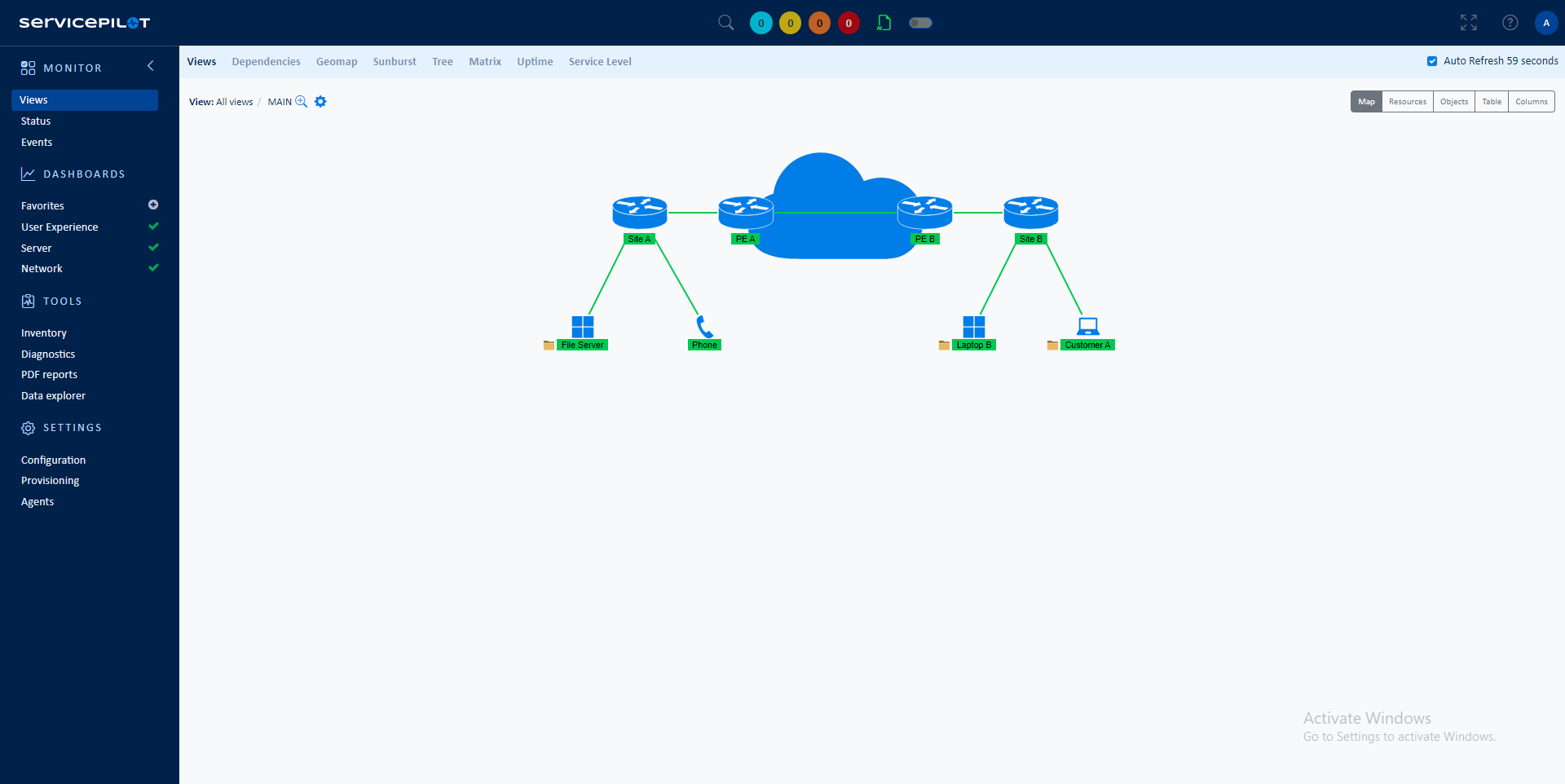
LAN and WAN network monitoring
In a constantly moving virtual world, speed, performance and availability are essential. The use of SaaS, VoIP and video is widespread, with tablets and smartphones multiplying constantly with the BYOD (Bring Your Own Device) generation bringing new loads on the network. With bandwidth-intensive applications, the performance of your network can degrade quickly and affect operational efficiency, user experience and business.
Learn moreCisco network monitoring
Cisco is known for its innovations and extensive range of network infrastructure solutions. To take full advantage of the technological advances offered by manufacturers in conjunction with your applications, it is essential to be able to interpret these indicators in order to measure the efficiency of the infrastructure application performance. ServicePilot oversees many Cisco switching, routing, virtualization, and advanced features such as IPSLA, Nbar, and CBQoS.
Learn more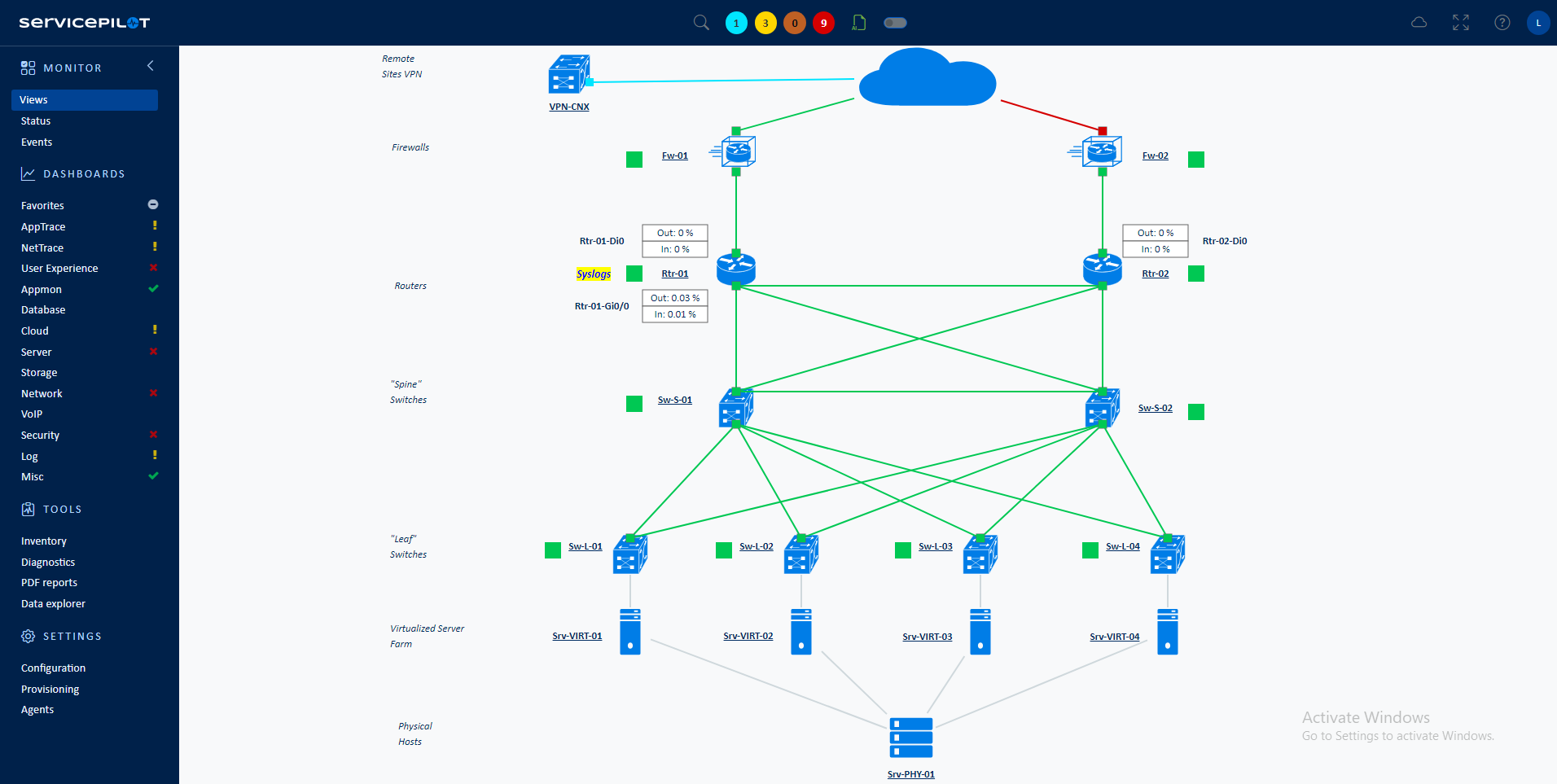
Wireless Wifi networks monitoring
In an increasingly mobile world, wireless networking technology is an essential productivity solution in the professional sphere allowing a user to stay connected while traveling within a limited or extended geographical perimeter. The resulting cabling savings are important and guests or customers appreciate being able to connect to the network. All these benefits should not turn into a security flaw for the company. ServicePilot monitors security and key performance indicators for WiFi networks.
Learn more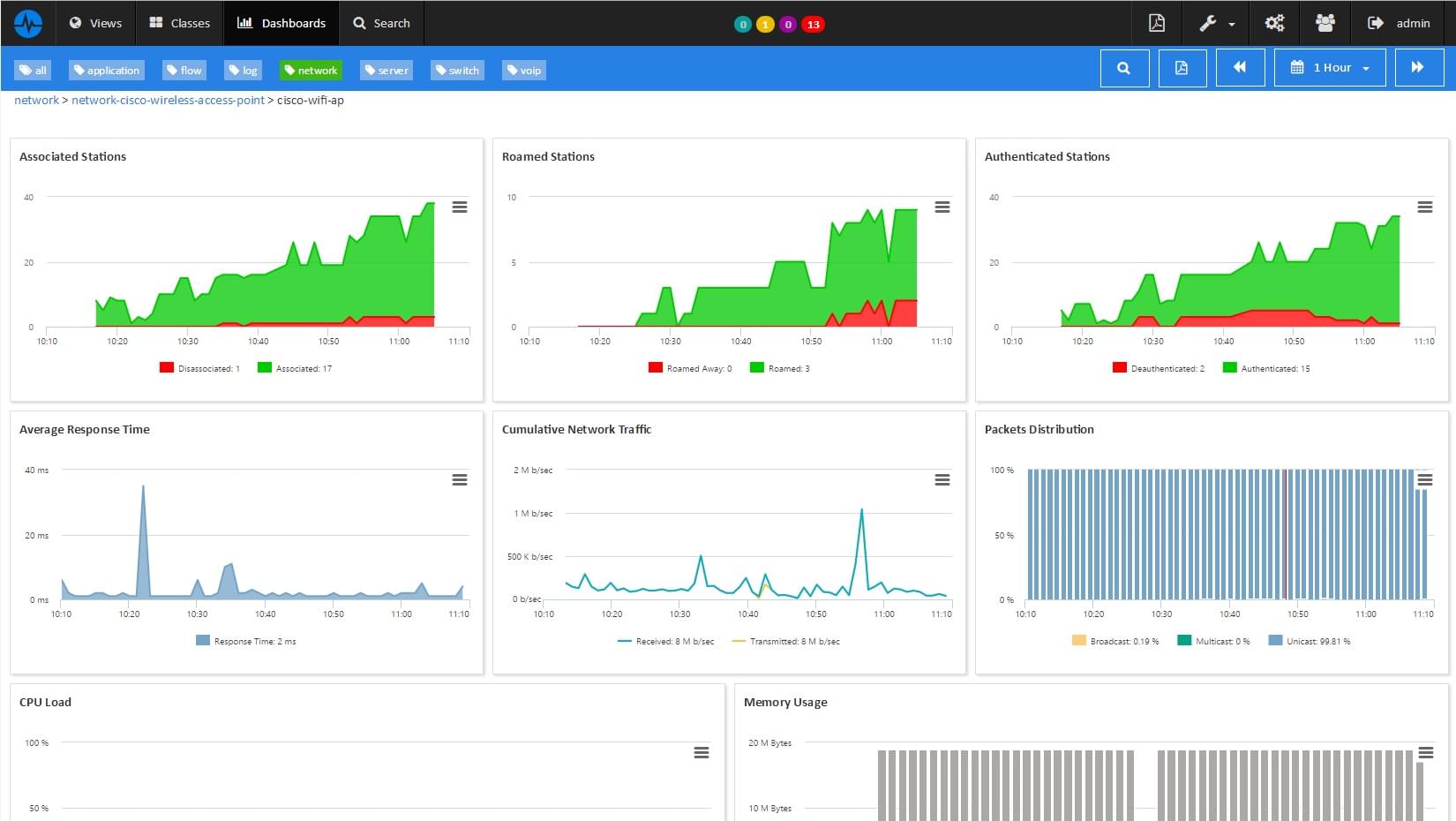
Analyzing trends and Capacity management: these are the keys to decrease of costs and incidents.
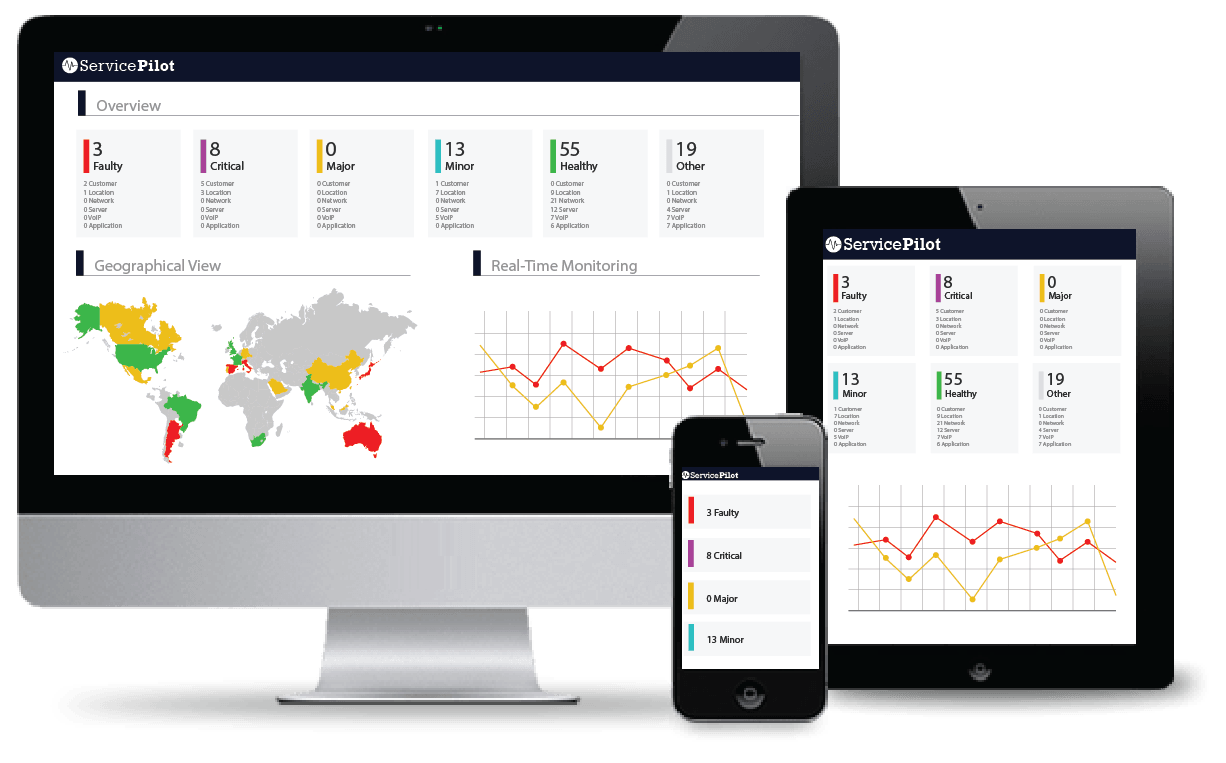
Our Management constantly asks us to ANTICIPATE problems and investments.
Thousands of devices on a map
Understand the organization of a network infrastructure of thousands of devices directly on a map and compare the performance of the equipment via appropriate dashboards.
Monitoring of all the equipment
Integrate all types of equipment to get an end-to-end view of the network infrastructure that must support your application's performance. Packages for different technologies (WAN, LAN, firewalls, ...) are available.
Automatic provisioning and discovery
Add or delete equipment in a file, the resources will be discovered automatically. They will be positioned or removed from geographic views without administrator intervention.
Capacity analysis for key indicators
Anticipate changes in network traffic to avoid saturation and performance degradation. The capacity planning features bring you trends for decision making.
Free installation in
a few clicks
SaaS Plateform
- No on-premise software setup, servicing and configuration complexity
- Instant setup, complete and pre-configured to ensure robust monitoring
OnPremise Plateform
- Contracts and commitments over time ( > 1 year)
- Performance, Data Storage and Infrastructure Management
- 2 additional solutions: VoIP and Mainframe monitoring
