What is Security Windows Sysmon?
Windows Sysmon, a component of the SysInternals suite, is a system service specifically designed for Windows operating systems. It delivers consistent monitoring and comprehensive logging for a diverse array of event types. Its capabilities include recording intricate details about process creations, network connections, registry events, and file creations, among others. Windows Sysmon stands out from Windows Events with its ability to track and log detailed event data. This extends from recording the creation of processes and network connections to tracking registry events and file creation. This level of detail enables network administrators and security teams to have a clear understanding of the actions taken within their IT environment.
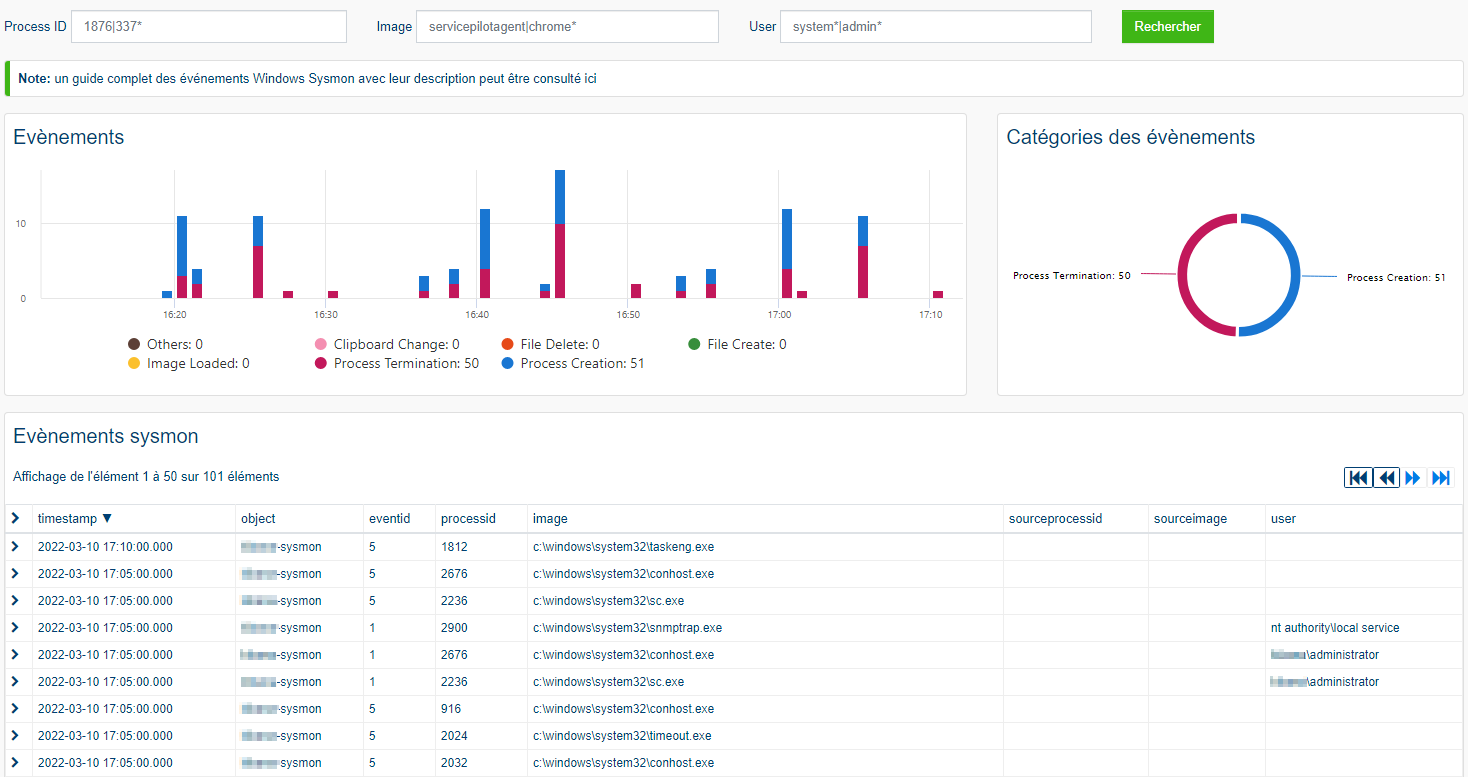
Monitoring Windows Sysmon is a critical task in maintaining a secure and efficient IT infrastructure. It facilitates the collection of detailed event data, which can be transmitted to platforms like ServicePilot using the Windows-Event package. These events can then be analyzed via the web interface, much like other standard Windows event logs. By integrating the detailed event data from Windows Sysmon with ServicePilot, organizations can significantly enhance their security monitoring capabilities with effective identification and management of malicious or abnormal activities. This integration provides a unified view of system events, which can streamline the process of identifying and mitigating potential security risks.
How to monitor Windows Sysmon?
ServicePilot makes it easy to monitor Windows Sysmon requiring only the installation of a ServicePilot Agent on the target server. A resource of the security-windows-sysmon package then needs to be added via the ServicePilot web interface.
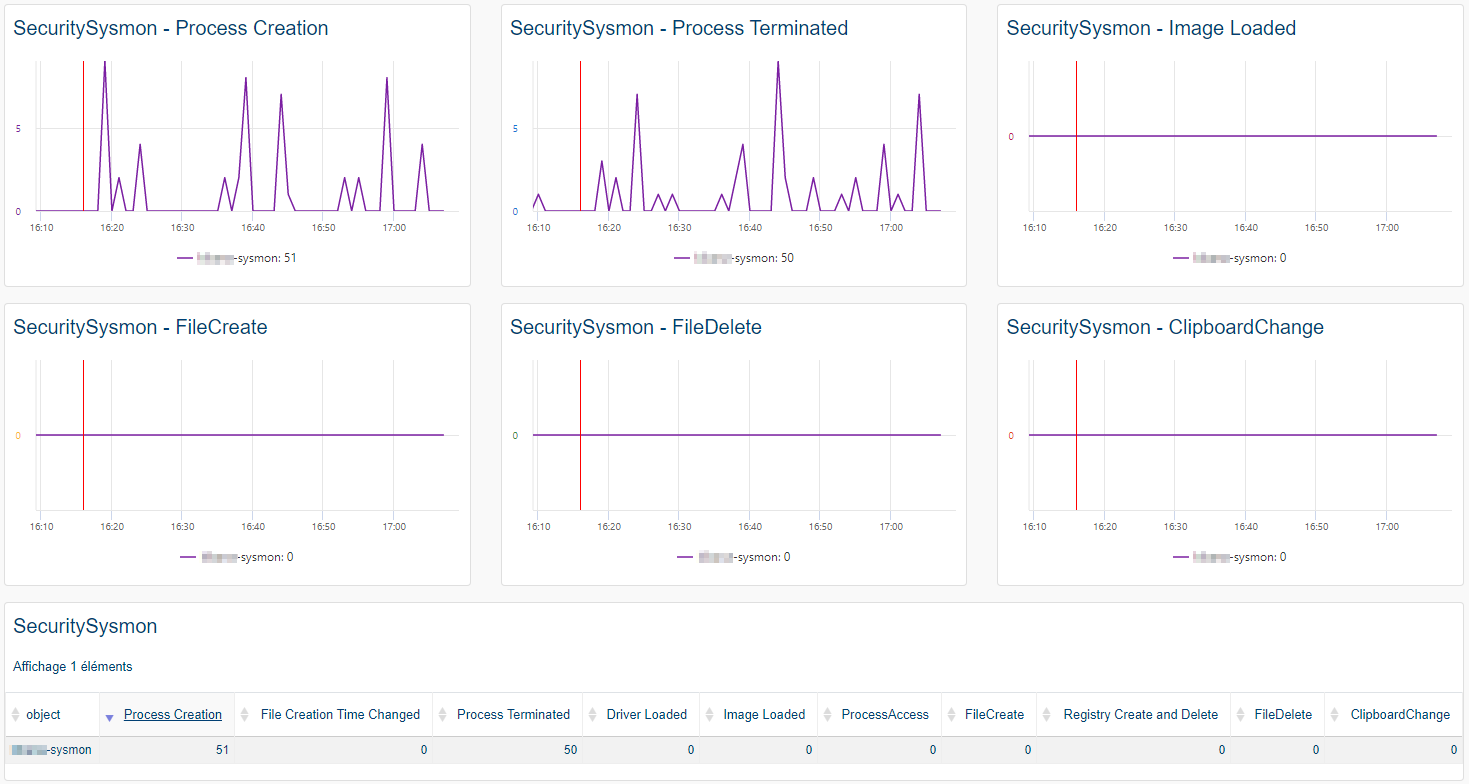
ServicePilot performs several predefined searches to automatically analyze data for all Windows systems sending Windows Sysmon Events collected by ServicePilot.
Different searches are carried out:
- Process Creation: the process creation event provides extended information about a newly created process
- File Creation Time Changed: the change file creation time event is registered when a file creation time is explicitly modified by a process
- Sysmon State Changed: the service state change event reports the state of the Sysmon service (started or stopped)
- Process Terminated: the process terminate event reports when a process terminates. It provides the UtcTime, ProcessGuid and ProcessId of the process
- Driver Loaded: the driver loaded events provides information about a driver being loaded on the system
- and others...
How to install a windows-sysmon resource?
- Use your ServicePilot OnPremise installation or a SaaS account.
- Add a new windows-sysmon resource via the web interface (
/prmviewsor/prmresources) or via API (/prmpackagespage), the default ServicePilot agent or another agent will be provisioned automatically.
Details of the windows-sysmon package are located in the
/prmpackagespage of the software.
Benefits
ServicePilot enables you to deliver IT services faster and more securely with automated discovery and advanced monitoring features.
By correlating the technology WINDOWS SYSMON with APM and infrastructure monitoring, ServicePilot is able to provide a more comprehensive view of an organization's IT environment.
This allows IT teams to quickly identify and diagnose issues that may be impacting application performance, and take corrective action before end-users are affected.
Start with a free trial of our SaaS solution. Explore our plans or contact us to find what works best for you.