What is Windows Event Search?
Once collected, detailed events of a Microsoft Windows Operating System (OS) can be automatically analyzed in the ServicePilot web interface with the Windows Event Search package.
Windows Event Search monitoring
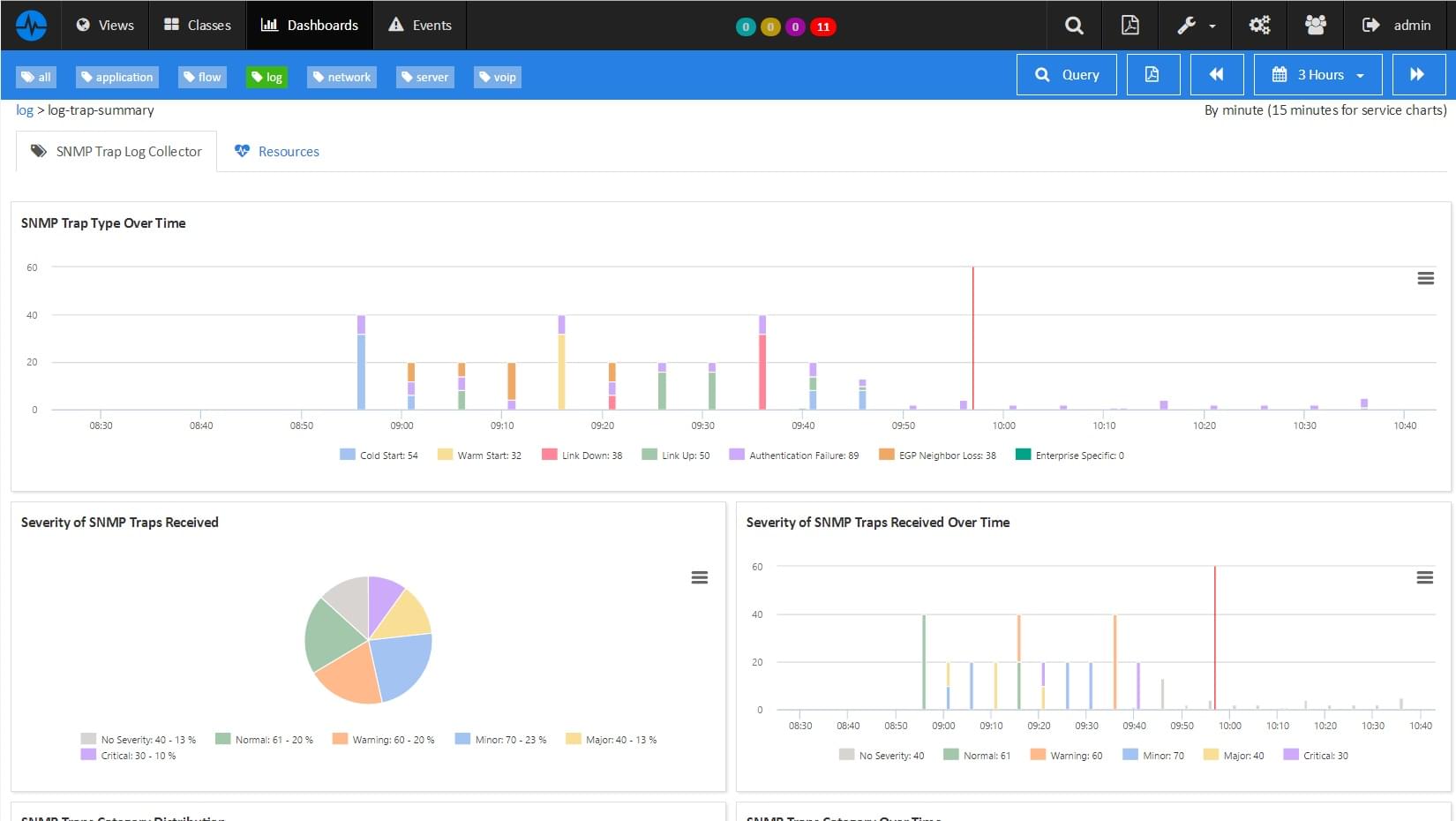
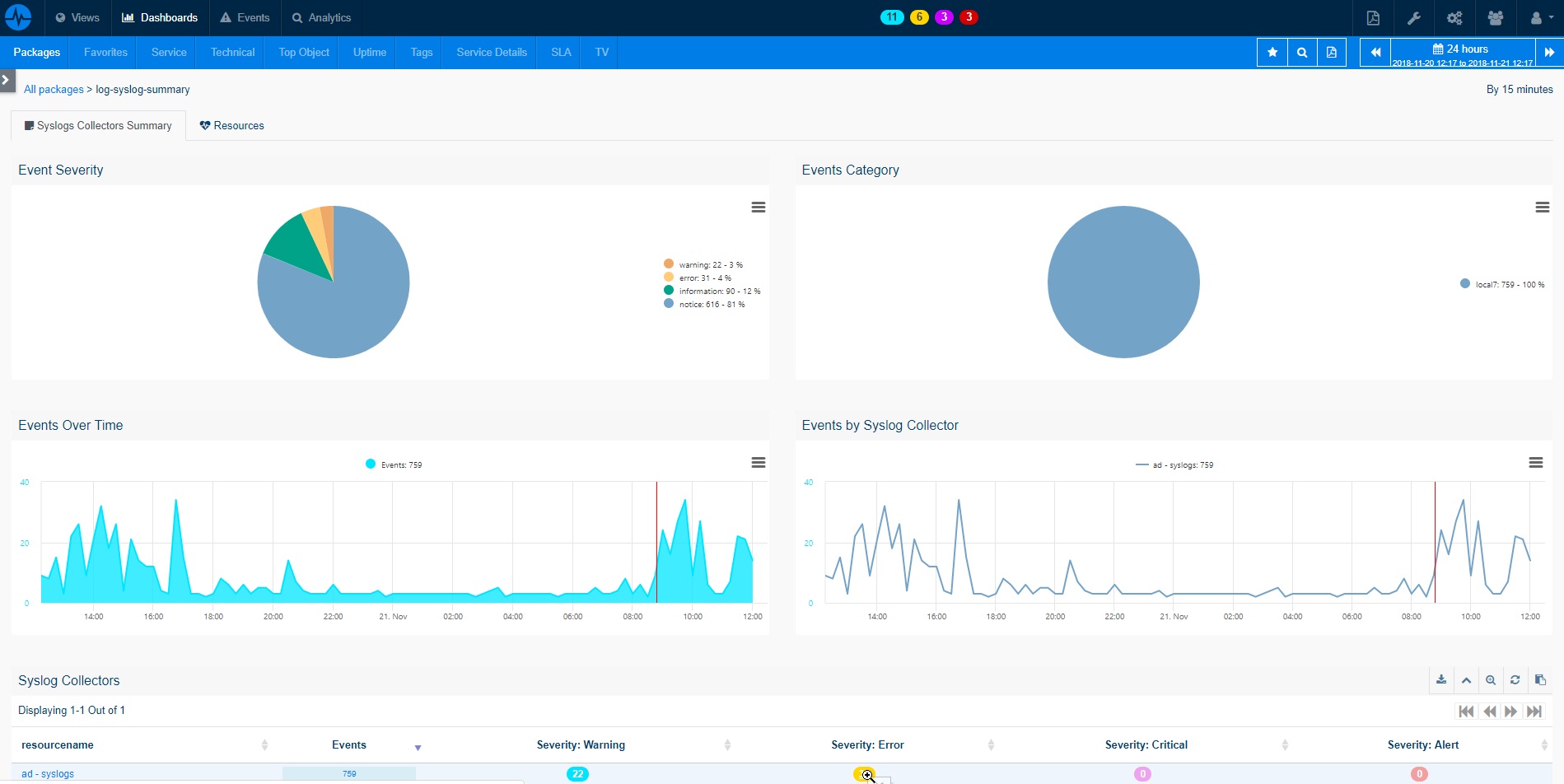
This package performs a variety of pre-built searches in order to automatically analyze data across every host forwarding Windows Events to ServicePilot.
Different types of searches are performed:
- Active Directory Critical Events: Monitors and triggers an alarm if any AD critical event occurs (1102, 4618, ...)
- User Login Failure Events: Monitors and alerts when users fail to log in (along with failed login reasons)
- Domain Controller Kerberos Authentication Events: Monitor Domain Controller and Kerberos critical events (failed Kerberos, DC logon, low encryption...)
- Password Change events: Monitors and matches user accounts for which password has changed
- and more...
Please note that for some searches, it also depends on the severity level or other filters on specific events that you established before forwarding events to ServicePilot.
How to install a windows-event-search resource?
- Use your ServicePilot OnPremise installation or a SaaS account.
- Add a new windows-event-search resource via the web interface (
/prmviewsor/prmresources) or via API (/prmpackagespage), the default ServicePilot agent or another agent will be provisioned automatically.
Details of the windows-event-search package are located in the
/prmpackagespage of the software.
Benefits
ServicePilot enables you to deliver IT services faster and more securely with automated discovery and advanced monitoring features.
By correlating the technology WINDOWS EVENT SEARCH with APM and infrastructure monitoring, ServicePilot is able to provide a more comprehensive view of an organization's IT environment.
This allows IT teams to quickly identify and diagnose issues that may be impacting application performance, and take corrective action before end-users are affected.
Start with a free trial of our SaaS solution. Explore our plans or contact us to find what works best for you.