IT Security Device Monitoring
Proactive Monitoring and Ensuring the High Performance of Firewalls
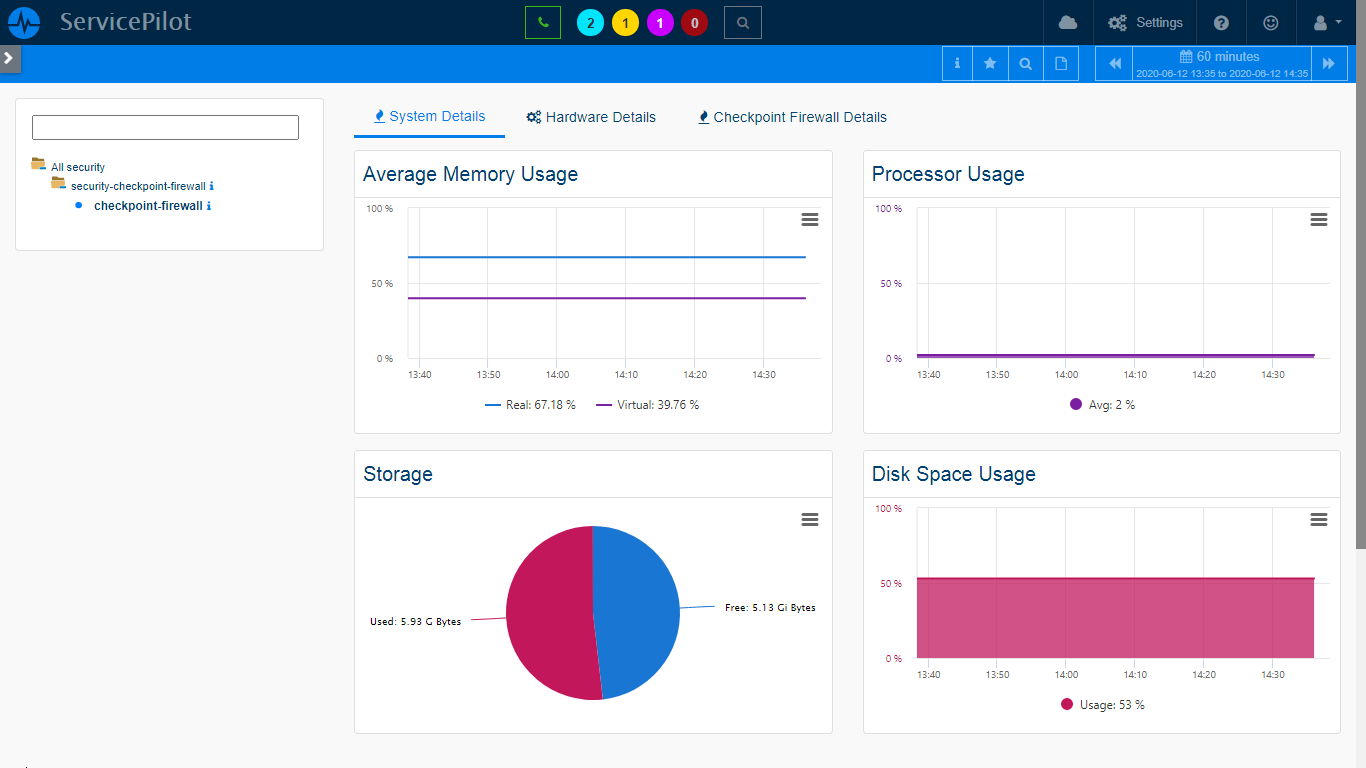
Firewalls are like the gatekeepers of a company's network so they need an accurate monitoring. With ServicePilot you can gather key indicators through SNMP polling coupled with log analysis. You will be able to check behavior patterns and the use of the most recent security policy updates. We offer ready-to-use packages to automate data collection and analysis for which will help you making informed decisions.
Let's consider a financial company with highly sensitive data. With our software, they can monitor constantly their firewalls, identify potential threats and ensure that the latest security policy updates are implemented.
- The key benefit of this feature lies in its proactive approach to network security
- With continuous monitoring of the firewall performance protect your network, enhance security and ensure business continuity
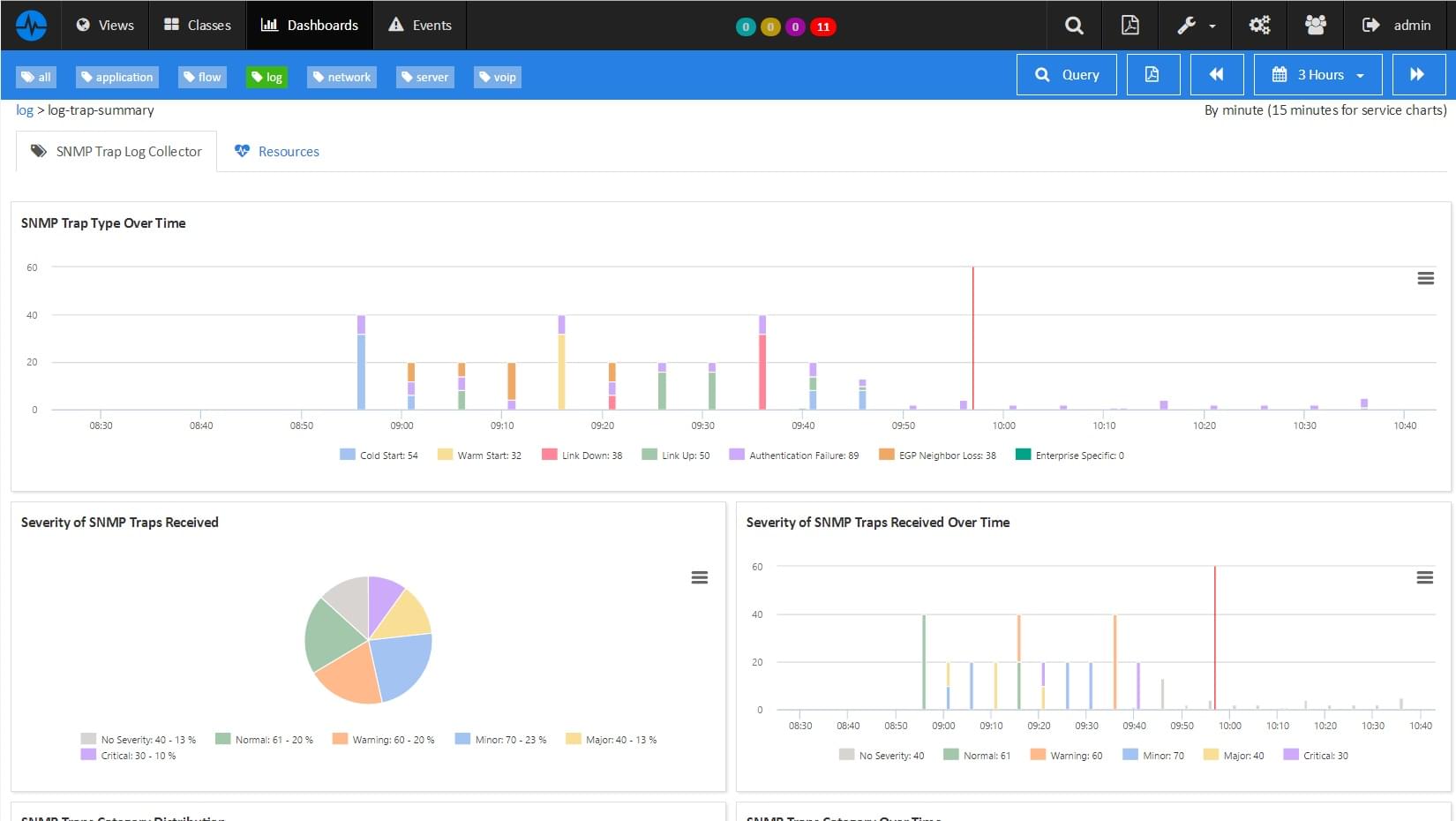
Detailed Analysis of IT Security Equipment and Services
We provide constant monitoring of various IT security devices that protect your data, applications, servers or network equipment. This approach is crucial to prevent security incidents. You can monitor the availability and performance of many IT security services like Proxies, Web or Messaging Gateways, IDS/IPS, VPN Access, DHCP, DNS and more.
An e-commerce company can use this feature to monitor their various security devices. This will ensure their customers' sensitive data remain secure.
- The main advantage of this feature is that it enhances your IT security posture.
- We provide in-depth monitoring of various IT security devices to allow you identify and address potential security issues in order to ensure optimal data protection
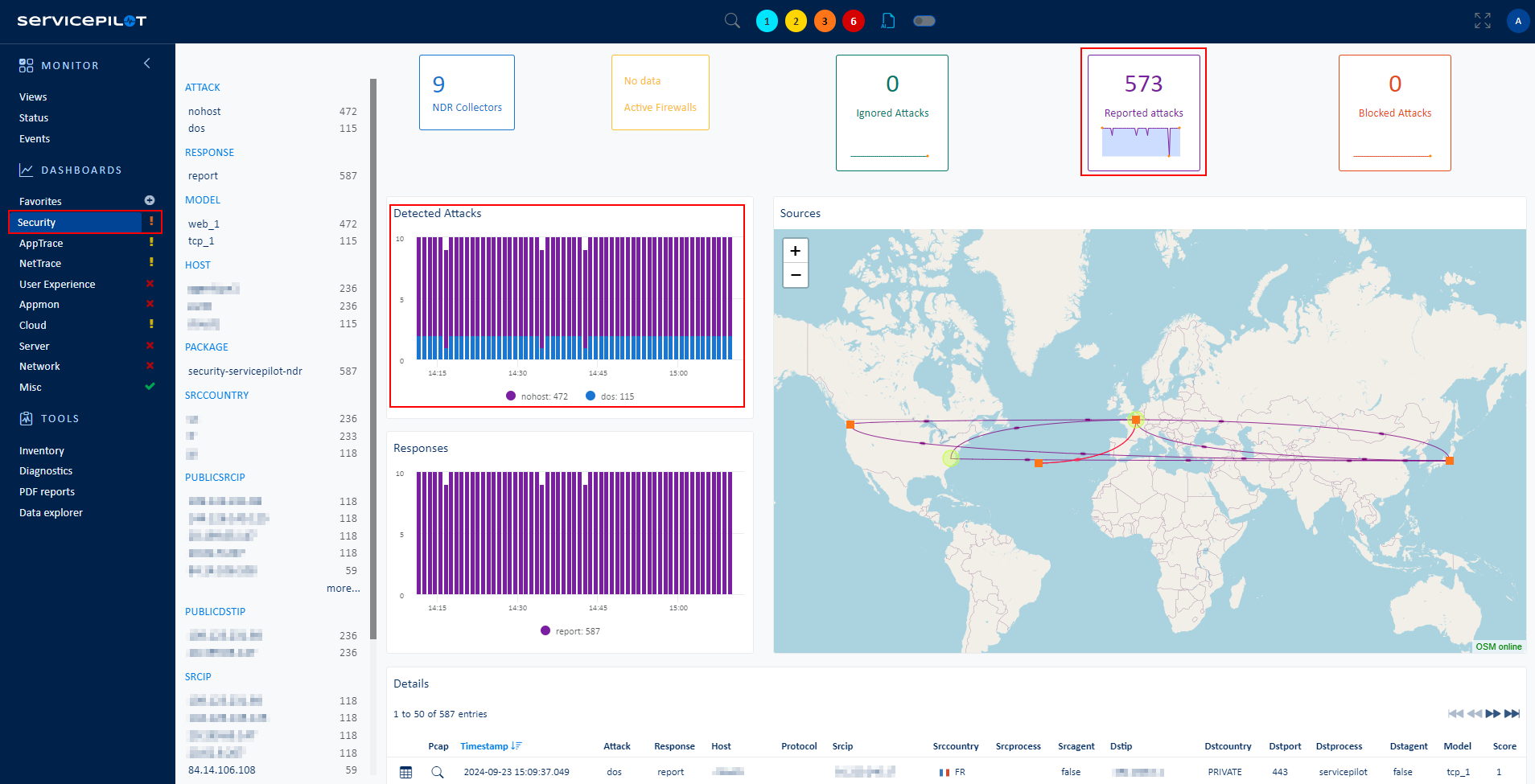
Extensive Monitoring of Other Security Services
Beyond IT, companies also deploy security devices like automatic barriers, identification gates, badge readers, security cameras and IoT devices for broader premises and data protection. They can customize packages to ease data collection and monitoring of these elements.
Consider a large factory with various physical security devices like badge readers and security cameras. These devices can be monitored to ensure that they are working properly and maintain the security of the site 24/7.
- The benefit of this monitoring is to provide a better view of your organization's security
- You can ensure the optimal functioning of all your security devices for a more secure business environment
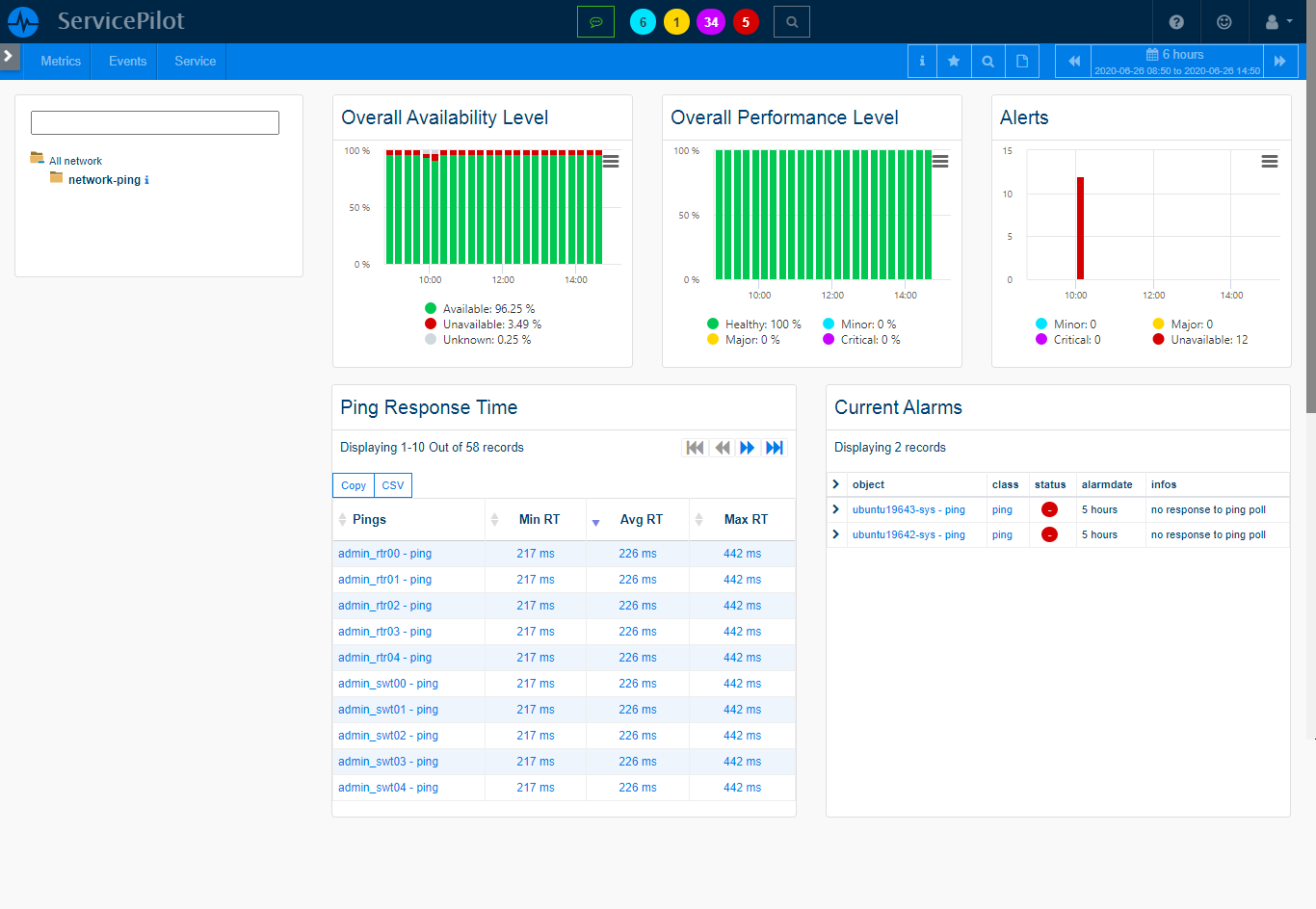
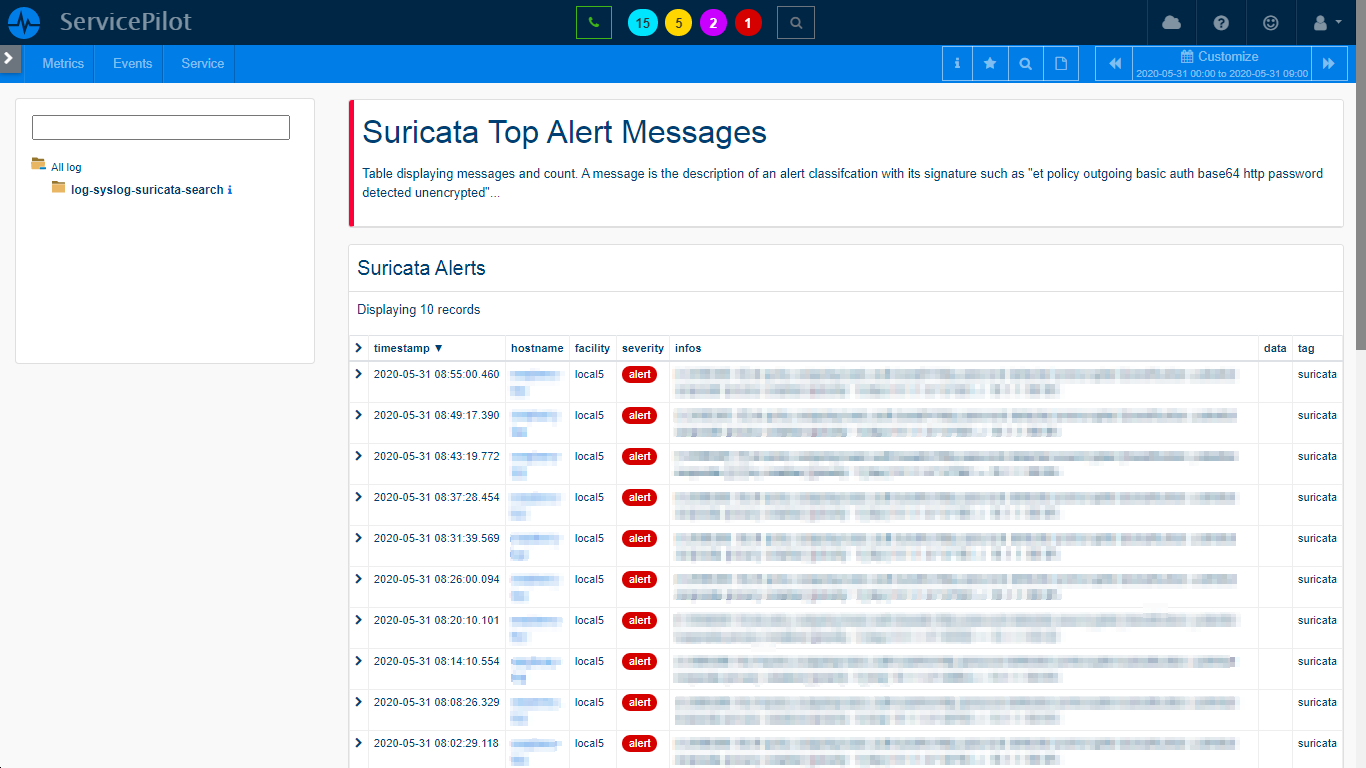
Correlating Security and Performance Data
Combining security and performance data is crucial for full insights into your IT environment. Our software captures KPI from various sources, including SNMP and analyzes logs to provide a holistic view of your IT operations. This correlation of data helps identify potential vulnerabilities rapidly and track the impact of security incidents on your overall IT performance and services.
Consider an online streaming service which requires high-performance servers to deliver a seamless experience to its users. You can correlate performance data with security logs and provides the IT team with detailed insights about any security incidents that may impact server performance. This could include a DDoS attack overloading the servers or a malware infection causing system instability.
- The main benefit of this approach is to provides a complete view of your IT and capturing the dependencies between security and performance
- This not only helps to identify and rectify potential issues swiftly but also eases the optimization of IT services to maintain business continuity
We were looking for a powerful tool, covering all of our server and application monitoring. A tool that could scale with us and that was reasonably priced.
Robust Security Monitoring with ServicePilot
IT Security
Analyze all your log sources with the same monitoring solution, enabling you to identify and locate multiple threats.
Compliance
Be assisted in fulfilling legal requirements to ensure compliance and avoid potential legal problems.
Threat Mapping
You can analyze event logs to find potential issues in your organization to promote a secure and threat-free environment.
Proactive Surveillance
Ensure that you keep the door closed to potential intruders and maintain a robust security posture.
Log and security Management integration
Other Log Management Solutions
Free installation in
a few clicks
SaaS Plateform
- No on-premise software setup, servicing and configuration complexity
- Instant setup, complete and pre-configured to ensure robust monitoring
OnPremise Plateform
- Contracts and commitments over time ( > 1 year)
- Performance, Data Storage and Infrastructure Management
- 2 additional solutions: VoIP and Mainframe monitoring